Investigating Sadistic Online Exploitation (SOE): Avoiding Vicarious Trauma and No Touch Research
Content Warning: This material contains offensive language and potentially sensitive topics that some (most) readers may find disturbing.
While investigating a particularly despicable topic for an OSINT project, Sarah followed what appeared to be a harmless link to a small video-sharing site. It was supposed to be just another niche platform — one of the countless obscure sites you run across in this kind of work. Instead, its front page displayed disturbing content she never expected, and certainly never meant to encounter. The site has since been reported, but the impact of stumbling across something you can’t unsee takes time to process.
This experience serves as a reminder that even the most unassuming corners of the internet can conceal traumatic material. In OSINT work, a link isn’t always what it appears to be, and even an obscure social media site can cater to a niche you never want to meet. Stay cautious, stay prepared, and always take care of yourself when the unexpected happens.
By Sarah Womer
The following are some tips on how to identify suspected extremist entities that may be engaged in Sadistic Online Exploitation (SOE) for investigative research leads, without having to view the graphic content through no-touch research that can be pivoted from for further investigation. The following example shows how to avoid visual vicarious content by avoiding graphic imagery and how to bypass touching the source. Step 5 in this example involves identifying Telegram users who may engage in SOE. Absolutely no graphic images are shown (and none were accessed). Still, the topic is upsetting, as the text indicates online locations that may sell and share footage of SOE, possibly including footage of children. The general topic of SOE is upsetting and can cause trauma in and of itself for some readers, even in mainstream print news media.
Please note that some search engines may be alerted for researching contentious topics. If this is of concern, an isolated container or virtual machine should be considered (these options provide better OSPEC anyway). In this example, SOE entities are indicated in Gore communities. The Gore domains discussed in this example may compromise a user's computer operating system if opened. The example Gore domains were not accessed for this article.
Step 1: Identify Related Unique Images or Phrases. Multiple research and news articles have recently been published reporting on 764 and SOE. A basic image search query was conducted using the term "764," and the resulting images were then scanned to determine if any extremist logos might be present in academic and news reporting. An extra and important safety step is to set search engine filtering options to ensure that graphic images are excluded.
The logo image below was selected for a Reverse Image Query from the viewed images. The URL of the logo was not opened, and the image was copied via screen capture.
Step 2: Scan but DO NOT open the URLs that contain the logo of the extremist SOE concept under consideration to see if any of the URLs look unique (unique in this sense being not news or investigative research and that may be engaged in an investigative topic).
Step 3: Check if the text concept of interest is discussed on the domains of the identified unique URLs that feature the Logo of interest. In some instances, using more than one Search Engine that supports the "site:" operator function is beneficial for reviewing a particular URL. The query results may vary depending on the algorithm, relevance formulas, and other factors that a search engine provider may use. For example, Kagi and Brave may provide different data on the same query.
Step 4: After identifying a URL of potential interest, run it through the tools that can assist in identifying research pivots with human analysis. Select tools that would ensure that your system does not touch the domain of the URL of interest. Step 4 in this example used several different tools, which provided pivotable information for an investigation. The tools utilized would vary depending on the URL target, and not all tools of use have been covered in this brief example. Below are three of several tools utilized. Other tools used included Who Is Lookups, Internet Archive, and BuiltWith (and other options were, of course, available). The most important part of this step is the human analysis of the tool findings.
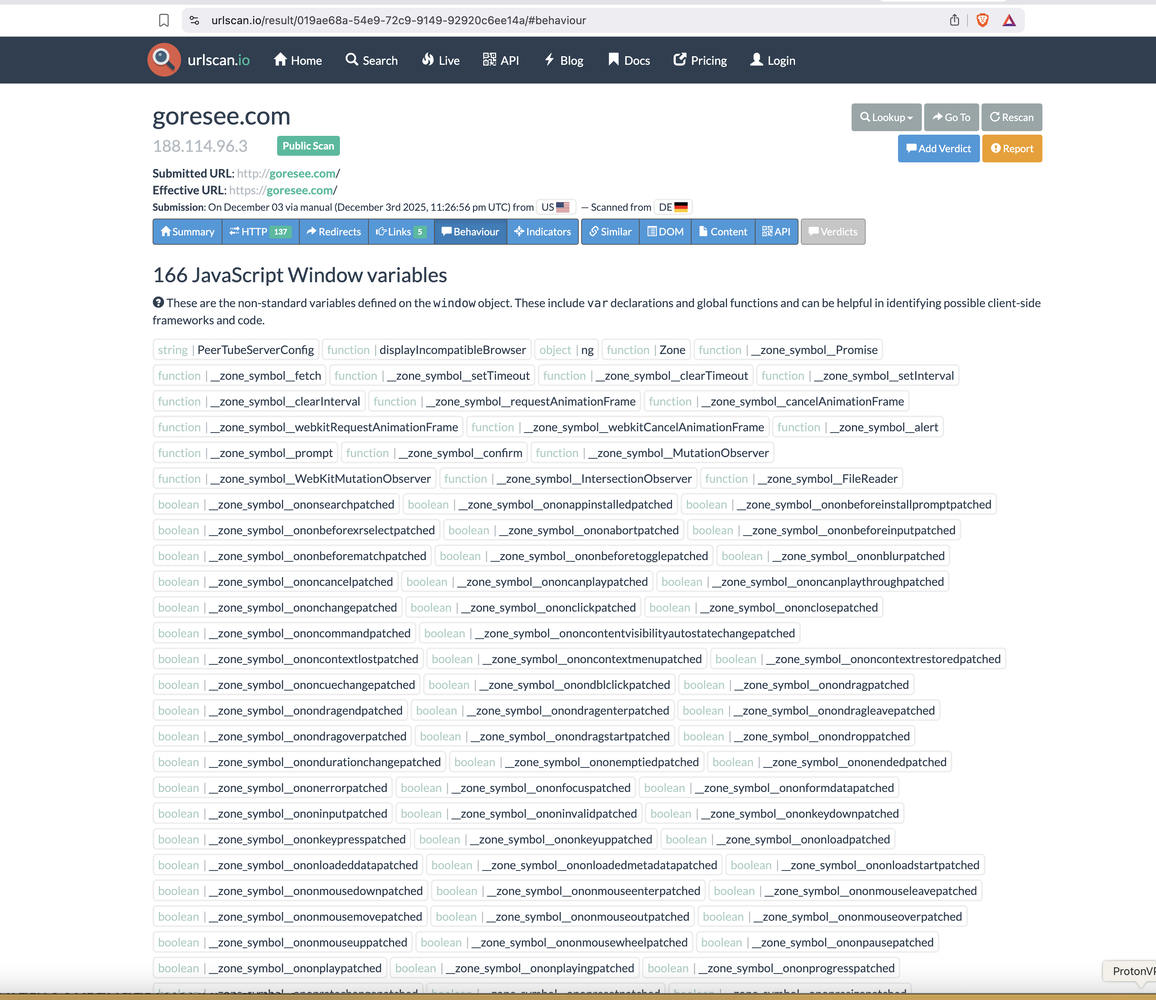
Step 4A: Query on URL with Fou Analytics Page XRay on the Identified Unique URL of "GoreSee" = Gore See
Pivot 4A1: The domain has browser fingerprinting and is U.S.-based
Can the browser fingerprinting data be legally and publicly dorked?
Can data from the domain browser fingerprinting be requested?
Can other tracking data be requested or collected?
Pivot 4A2: Pivots from JSON can be MANY, depending on what is provided in the files (For example, the view file showed the queried page was last updated on "Tue, 09 Sep 2025 09:13:28 GMT"
Pivot 4A3: Screenshot of URL without touching the domain (Caution with this option if graphic images may be present)
Pivot 4A4: View entities that are tracking and collecting on the site that are not the domain. Can that data be accessed, and what can it be used for? For example, Malwarebytes states that one of the trackers on this domain is commonly used for PUPs, scams, and adware, and has been used with hijacks in the past (Malwarebytes.com). A pivot query from this point showed that Goresee is blacklisted by some security vendors and is considered a high-risk website and domain. Sophos marked Gorsee as Malware, and Grindinsoft has marked it as suspicious. CRDF has also stated that Gorsee is a malicious URL (URL Void, Virus Total).
Pivot 4A5: PeerTube (on Fediverse Activity Pub) was identified as an external link to the Domain via Fou Analytics Page X-Ray, as was the GitHub OS repository for PeerTube. Additionally, the Har JSON file confirmed that the domain utilizes PeerTube. In addition, the domain checks a user's browser to see if it is compatible with PeerTube (Internet Archive also confirmed that the Domain utilizes PeerTube. No images were viewed when utilizing Internet Archive in this usage case.)
A Telegram link was also indicated in the External Links section, which may be of interest.
Step 4B: Query on URL Scan IO. Multiple pivots are available from this query. The query response screenshot below shows a few of the numerous pivot potentials.
In the above example, the two Telegram Outgoing URLs are of interest for possible investigative use.
Step 4C: Query URL on a Backlink Checker. Several backlinks were identified that may also be of interest for SOE investigations, providing investigative lead pivots. Ahrefs was used for the following example. A reference publication was identified via backlinks by Grey Dynamics that may be of use. Another identified backlink from an Incel Forum provided an entire list of possible sites dedicated to Gore, with some potentially containing SOE that could provide additional investigative pivots.
Step 5: Identify Telegram Accounts of Goresee Users via Search Engine Query. Telegram was established as being used on Goresee in Step 4.
Step 5A: Identify Telegram Users on Goresee that May Be Engaged with SOE
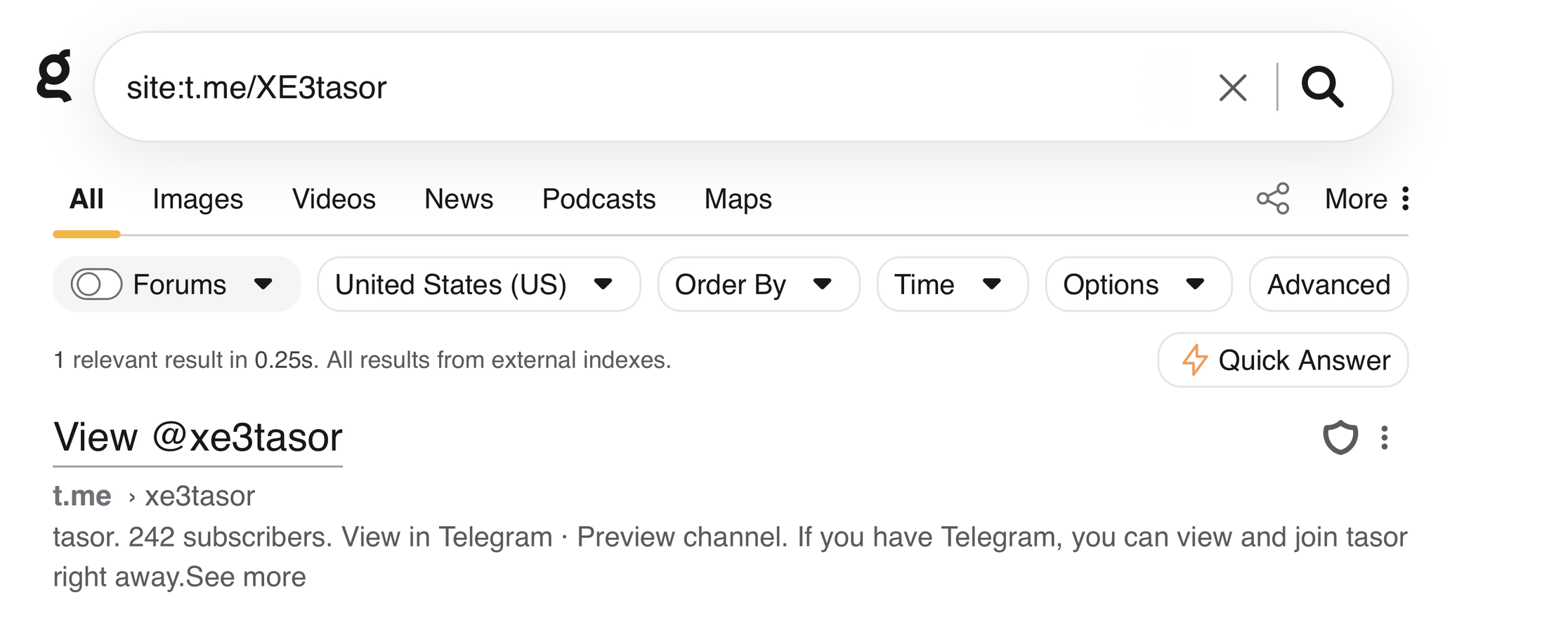
Step 5B: An example pivot of viewing information about one of the Telegram accounts engaged in Goresee without touching the Telegram account with Kagi Search. In this step, Brave did not provide useful query results.
Tasor R36 on Telegram was selected for this example, as the above Telegram Accounts query result indicated a possible child SOE with the phrase "child pain." A quick query via Kagi reveals that users in this Telegram account are selling items and that pornographic and adult content are present. Kagi AI summarizer was also used to give a peripheral text tip about the content surrounding the Telegram account. Additionally, at least two other locations that mention this Telegram account (viewable via Kagi) indicate possible SOE, and one even mentions a "Snuff Mixtape." Snuff films and tapes are purported to depict the murder of humans for sadistic exploitation. Both of these accounts were also reported to a cyber tipline. Users who encounter accounts during the course of their research that may be harming children have several reporting options. For U.S.-based researchers, the National Center for Missing and Exploited Children is a primary tip line venue, https://report.cybertip.org.
This example demonstrates that potentially useful qualitative data can be collected for the analysis and investigation of suspected SOE entities without requiring direct contact or visual inspection of disturbing imagery, and SOE, for portions of an investigation. Once you see something on the Internet, you can't "unsee it." The above steps show some, not all, ways of avoiding imagery that could cause visual vicarious trauma and that may compromise OPSEC in an investigation. Additional measures can also be taken, such as stripping imagery or videos from a source before viewing it. This example also demonstrates how easily one can pivot from a phrase or image in an article to suspected extremist niche communities, entities, or topics. SOE and CSAM images can also put an investigator in legal jeopardy if appropriate research measures and permissions are not in place. Removing the images helps protect the researcher.
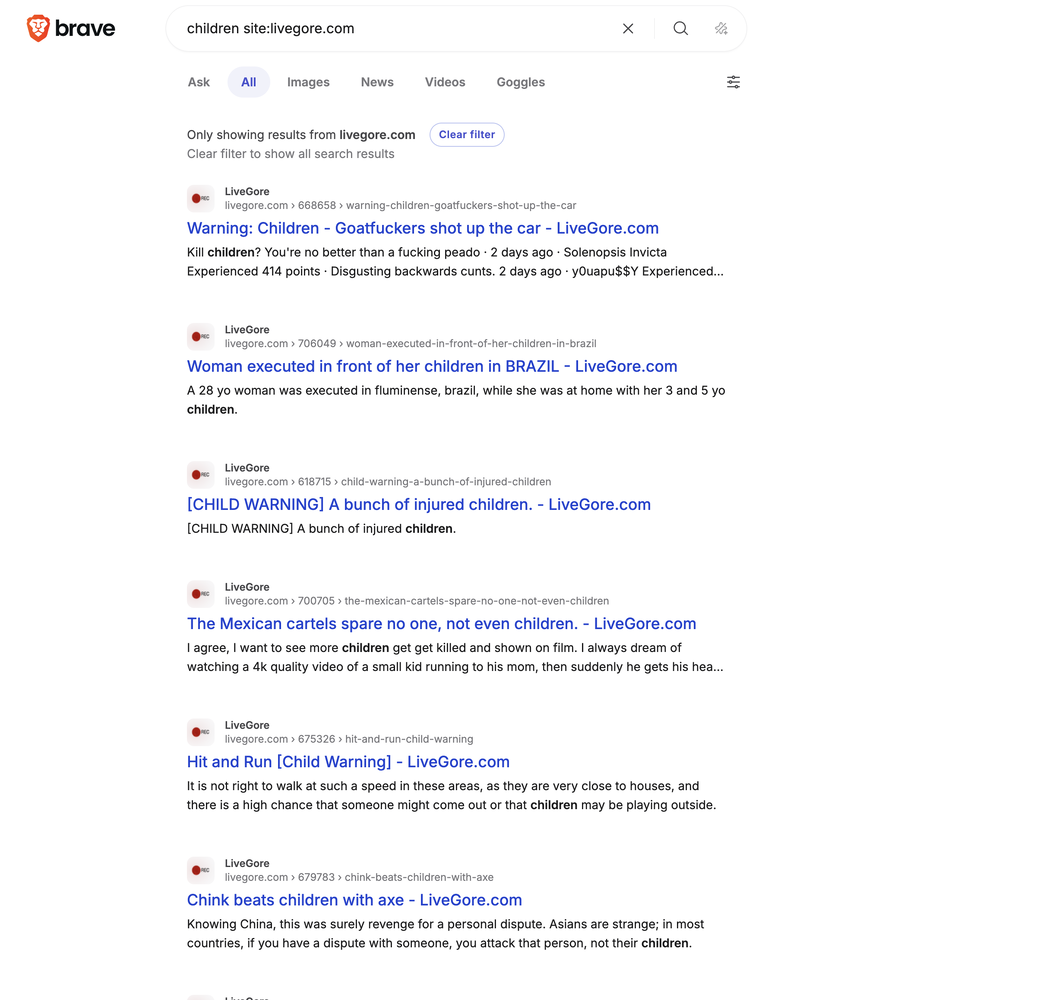
Several URLs were omitted from this example that may contain affiliated concepts and data. Two notable URLs that also may have relevant materials under their domains, as it relates to 764 and SOE, are livegore [dot] com and gorecenter [dot] com.) Both domains are described as containing disturbing materials, and the absence of image views, along with no-touch research techniques, would also be useful for generating investigative leads.
Supplemental on Step 1: Identify Related Unique Images or Phrases (as it relates to child SOE)
Example posts that may indicate SOE predatory behavior.